Cybersecurity News
Stay informed about the latest cybersecurity incidents, vulnerabilities, and threat landscape changes. We cover data breaches, ransomware campaigns, critical CVEs, and regulatory updates – with context on what it means for you and how to protect yourself.
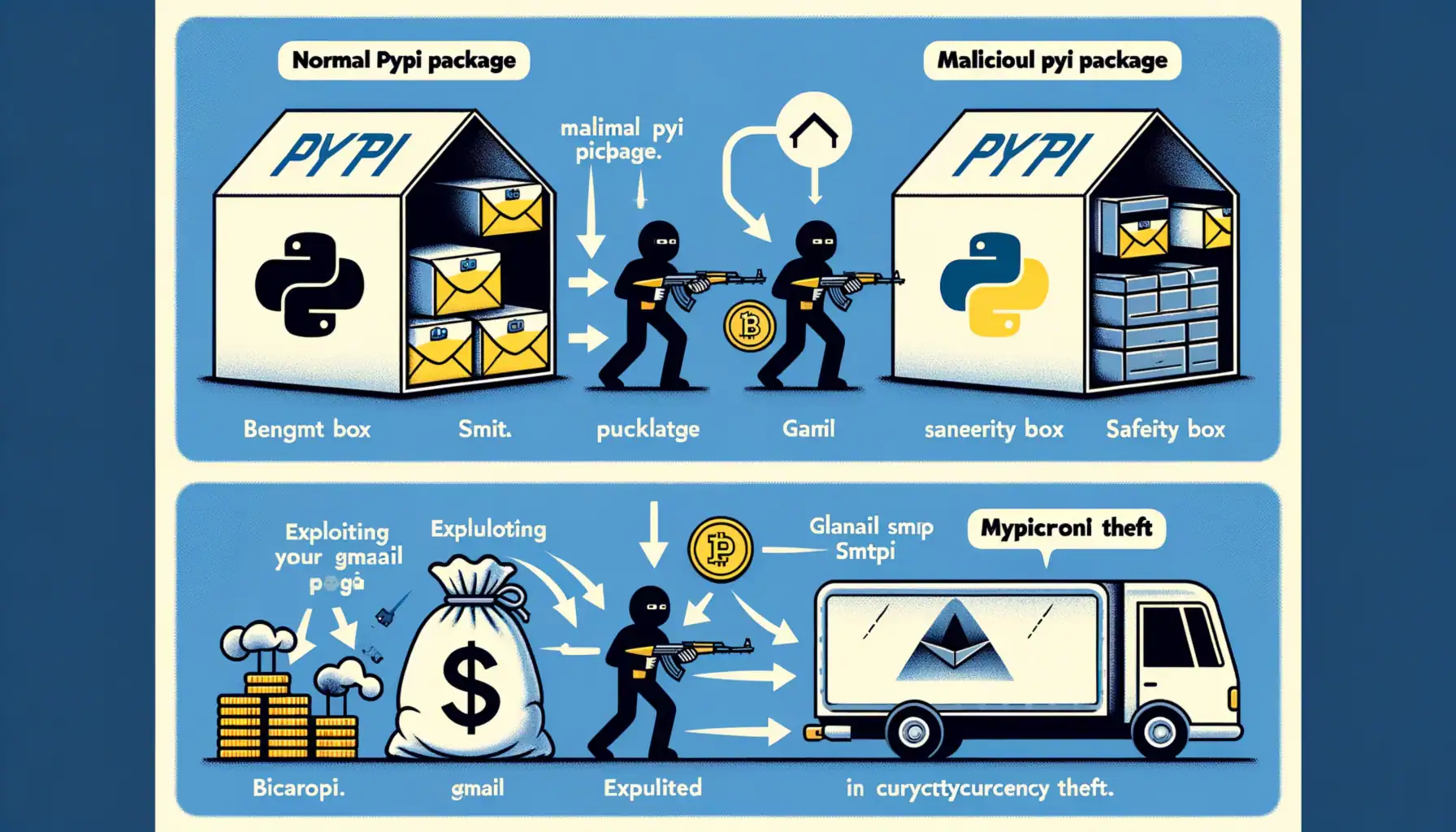
Sophisticated PyPI Attack Campaign Leverages Gmail SMTP Servers to Evade Detection
Security researchers at Socket have uncovered a sophisticated attack campaign targeting the Python Package Index (PyPI), revealing seven malicious packages ...

Critical Security Breach Reveals Vulnerabilities in Enterprise Messaging Platform TeleMessage
A significant cybersecurity breach has exposed critical vulnerabilities in TeleMessage’s enterprise messaging infrastructure, compromising sensitive communications from government agencies and ...

Google Releases Emergency Android Security Patch to Address Critical FreeType Vulnerability
Google has released an urgent security update for Android, addressing 46 vulnerabilities, with particular emphasis on a critical FreeType library ...

Critical Supply Chain Attack on Magento Ecosystem Affects Hundreds of Online Stores
Cybersecurity researchers at Sansec have uncovered a sophisticated supply chain attack targeting the Magento e-commerce ecosystem, affecting between 500 and ...

Security Researchers Uncover Major Windows RDP Authentication Vulnerability
A significant security vulnerability has been discovered in Windows Remote Desktop Protocol (RDP) that could potentially compromise enterprise security. Security ...
Record-Breaking DDoS Attack Trends: Cloudflare’s Latest Cybersecurity Analysis
Cloudflare’s latest security report reveals an alarming escalation in DDoS (Distributed Denial of Service) attack activity, with the company intercepting ...

DOJ Charges Alleged Black Kingdom Ransomware Operator in Global Exchange Server Attacks
The U.S. Department of Justice has announced criminal charges against Rami Khaled Ahmed, a 36-year-old Yemeni national, for allegedly developing ...
Security Researchers Uncover Dangerous Go Modules Targeting Linux Systems
Security researchers at Socket have discovered a critical cybersecurity threat targeting Linux systems through three malicious Go modules. These sophisticated ...

Major Security Breach: xAI Employee Accidentally Exposes Confidential API Key on GitHub
A significant cybersecurity incident has emerged at xAI, where an inadvertent exposure of a confidential API key on GitHub potentially ...

Microsoft Makes Passwordless Authentication Default for New Accounts: A Cybersecurity Milestone
Microsoft has announced a groundbreaking shift in user authentication protocols, making passwordless login the default option for all new accounts ...






