Cybersecurity News
Stay informed about the latest cybersecurity incidents, vulnerabilities, and threat landscape changes. We cover data breaches, ransomware campaigns, critical CVEs, and regulatory updates – with context on what it means for you and how to protect yourself.

Nike Data Breach: World Leaks Claims Massive Theft of Internal Files
Nike is conducting an internal investigation following claims by the cybercriminal group World Leaks that it has compromised the company’s ...

Microsoft Office CVE-2026-21509: What You Need to Know About the New Critical Vulnerability
Microsoft has issued an out-of-band security update to address CVE-2026-21509, a critical Microsoft Office vulnerability that is already being exploited ...

CVE-2026-24061: Critical GNU InetUtils Telnetd Vulnerability Under Active Attack
The critical vulnerability CVE-2026-24061 in the GNU InetUtils telnetd server component is already being exploited in real-world attacks. Rated 9.8 ...

Stanley Malware-as-a-Service: Malicious Browser Extensions Bypassing Store Security
A newly identified malware-as-a-service (MaaS) platform called Stanley is offering cybercriminals ready-made malicious browser extensions with a promise that they ...
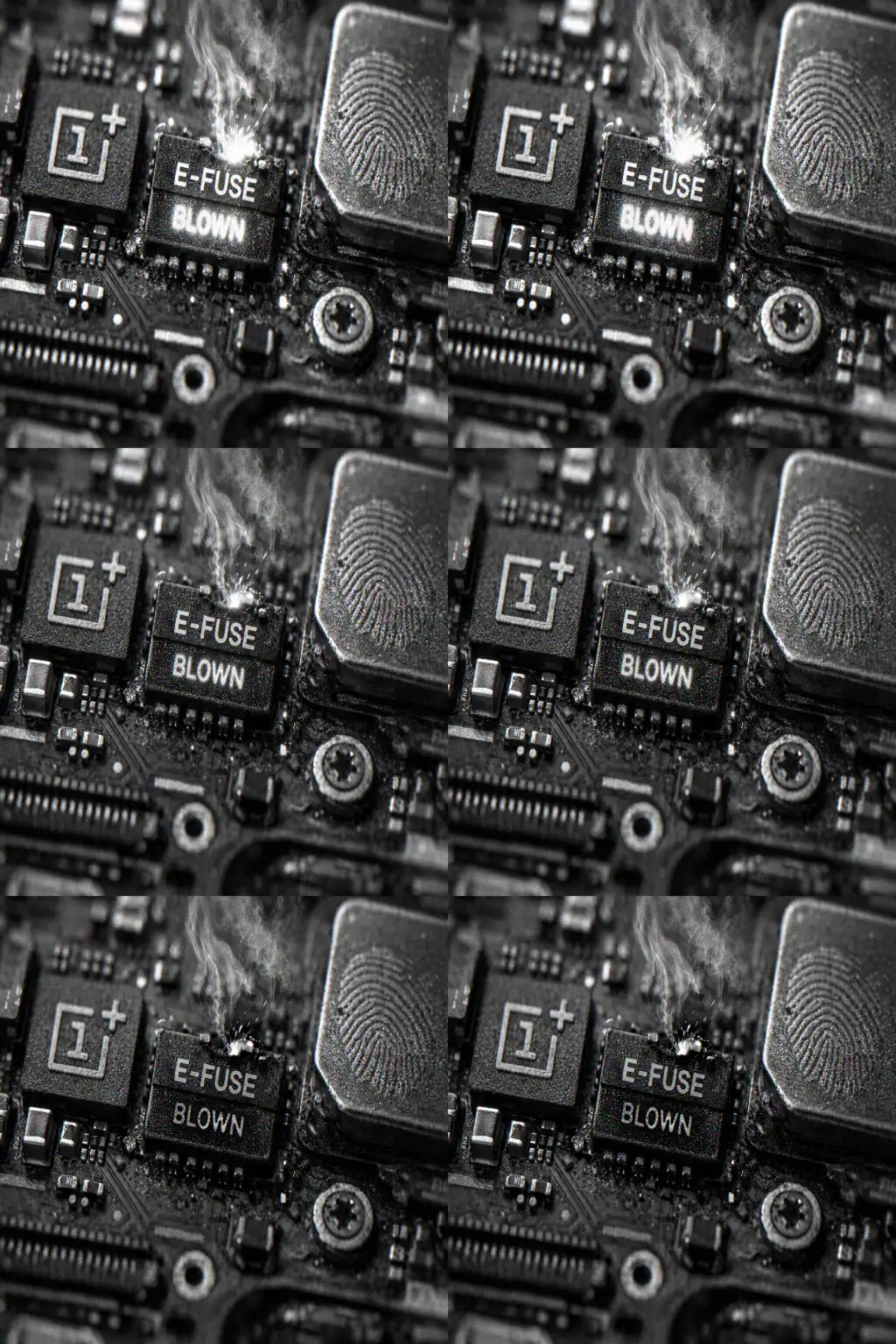
OnePlus Enables Hardware Anti-Rollback Protection in ColorOS, Putting Downgrades and Custom ROMs at Risk
Recent ColorOS builds for new OnePlus flagships introduce a strict hardware-backed Anti-Rollback Protection (ARB) mechanism that can effectively block downgrades ...

Malicious VS Code AI Extensions Steal Source Code in MaliciousCorgi Campaign
Two malicious AI coding assistant extensions have been discovered in the official Visual Studio Code Marketplace, collectively amassing roughly 1.5 ...

1Password Introduces Built-In Phishing Protection for Suspicious and Look-Alike URLs
Phishing remains one of the most effective techniques for stealing passwords, even among users who rely on password managers. In ...

Microsoft, BitLocker Recovery Keys, and Law Enforcement: Lessons from the Guam Investigation
In 2024, Forbes reported that Microsoft supplied law enforcement with BitLocker recovery keys to unlock Windows laptops seized in a ...

INC Ransomware: How Cyber Centaurs Recovered Victim Data from Attackers’ Own Backups
A rare incident response case has highlighted a critical blind spot in many organizations’ ransomware defenses. Cybersecurity firm Cyber Centaurs ...

GitLab Patches Critical 2FA Bypass and DoS Vulnerabilities: What DevSecOps Teams Must Know
GitLab has shipped out-of-band security updates to address a critical two-factor authentication (2FA) bypass and several denial-of-service (DoS) vulnerabilities in ...






