Cybersecurity News
Stay informed about the latest cybersecurity incidents, vulnerabilities, and threat landscape changes. We cover data breaches, ransomware campaigns, critical CVEs, and regulatory updates – with context on what it means for you and how to protect yourself.

Akira Ransomware Names Apache OpenOffice in Alleged Breach, but ASF Rejects Data Theft Claims
Akira ransomware operators have added Apache OpenOffice to their leak site, asserting they stole 23 GB of data containing employee ...

Edge 142 ties on-device ML to Defender SmartScreen for faster scareware blocking
Microsoft is expanding security in Edge by connecting its local, on-device scareware detector to the cloud-based Defender SmartScreen service. The ...

DOJ: Former Incident Responders Accused of Aiding BlackCat Ransomware
U.S. federal prosecutors have charged three individuals — including two former cybersecurity professionals — with allegedly compromising the networks of ...

Time‑Bombed NuGet Packages Target .NET Databases and Siemens PLCs, Socket Warns
Researchers at Socket report the discovery of nine malicious NuGet packages engineered with delayed activation designed to evade detection for ...

GlassWorm Plants Malicious VS Code Extensions in OpenVSX, Leveraging Unicode Tricks and Blockchain C2
Threat actors tracked as GlassWorm have again compromised the Visual Studio Code ecosystem by publishing three new malicious extensions to ...
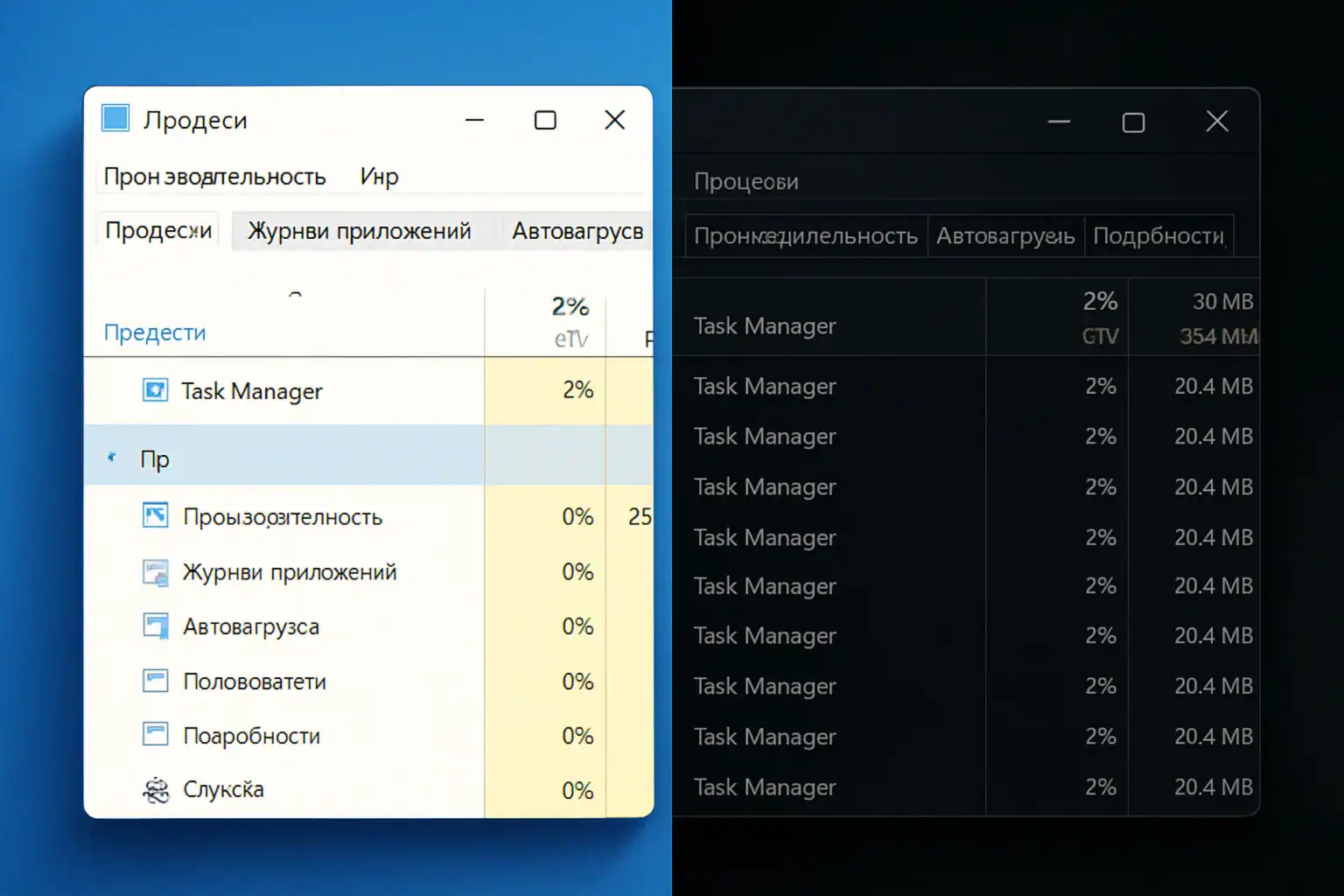
Windows 11 KB5067036 Leaves Task Manager Running in Background, Causing CPU and RAM Drain
Microsoft’s optional update KB5067036, released on October 28, 2025 for Windows 11 versions 24H2 and 25H2, introduces a regression that ...

AI-Powered Metamorphic Malware Emerges: Google GTIG Flags PromptFlux and Rising LLM Abuse
Google’s Threat Intelligence Group (GTIG) is tracking a notable shift in adversary tradecraft: threat actors are embedding large language models ...

LandFall: New Spyware Uses WhatsApp DNG Zero‑Click to Exploit Samsung Galaxy Zero‑Day (CVE‑2025‑21042)
Palo Alto Networks has identified a previously unknown surveillance platform, LandFall, that abused a zero‑day flaw in select Samsung Galaxy ...

Post SMTP CVE-2025-11833 is under active attack: update WordPress sites to 3.6.1+
Attackers are actively targeting WordPress sites via a critical vulnerability, CVE-2025-11833, in the widely used Post SMTP plugin (over 400,000 ...

Proofpoint: RMM-enabled phishing campaigns hijack logistics systems to reroute cargo
Threat researchers at Proofpoint are tracking a wave of targeted phishing operations against transportation and logistics providers that convert cyber ...






