Cybersecurity News
Stay informed about the latest cybersecurity incidents, vulnerabilities, and threat landscape changes. We cover data breaches, ransomware campaigns, critical CVEs, and regulatory updates – with context on what it means for you and how to protect yourself.

Anthropic Unveils Claude Code Security: AI-Powered Vulnerability Detection for DevSecOps
Anthropic has announced Claude Code Security, a new AI-driven capability designed to detect vulnerabilities in source code and propose fixes. ...

LLM-Powered Campaign Compromises Over 600 FortiGate Firewalls Worldwide
Amazon security specialists have disclosed a large-scale, targeted campaign against FortiGate firewalls in which a Russian-speaking threat actor compromised more ...

BeyondTrust CVE‑2026‑1731 Actively Exploited: CISA KEV Expansion and a Stealth Supply Chain Attack on Notepad++
Attackers are aggressively exploiting the critical vulnerability CVE‑2026‑1731 in BeyondTrust Remote Support (RS) and Privileged Remote Access (PRA), prompting the ...

North Korean Hackers Weaponize Google Gemini in Advanced AI-Driven Cyber Operations
Generative AI is rapidly shifting from a productivity tool to a powerful asset in the hands of cybercriminals. According to ...

Advanced Supply Chain Attacks on npm and PyPI: Lazarus‑Linked graphalgo Campaign and New Malware Waves
Open source ecosystems npm and PyPI have again become high‑value targets in a coordinated software supply chain attack. Cybersecurity researchers ...
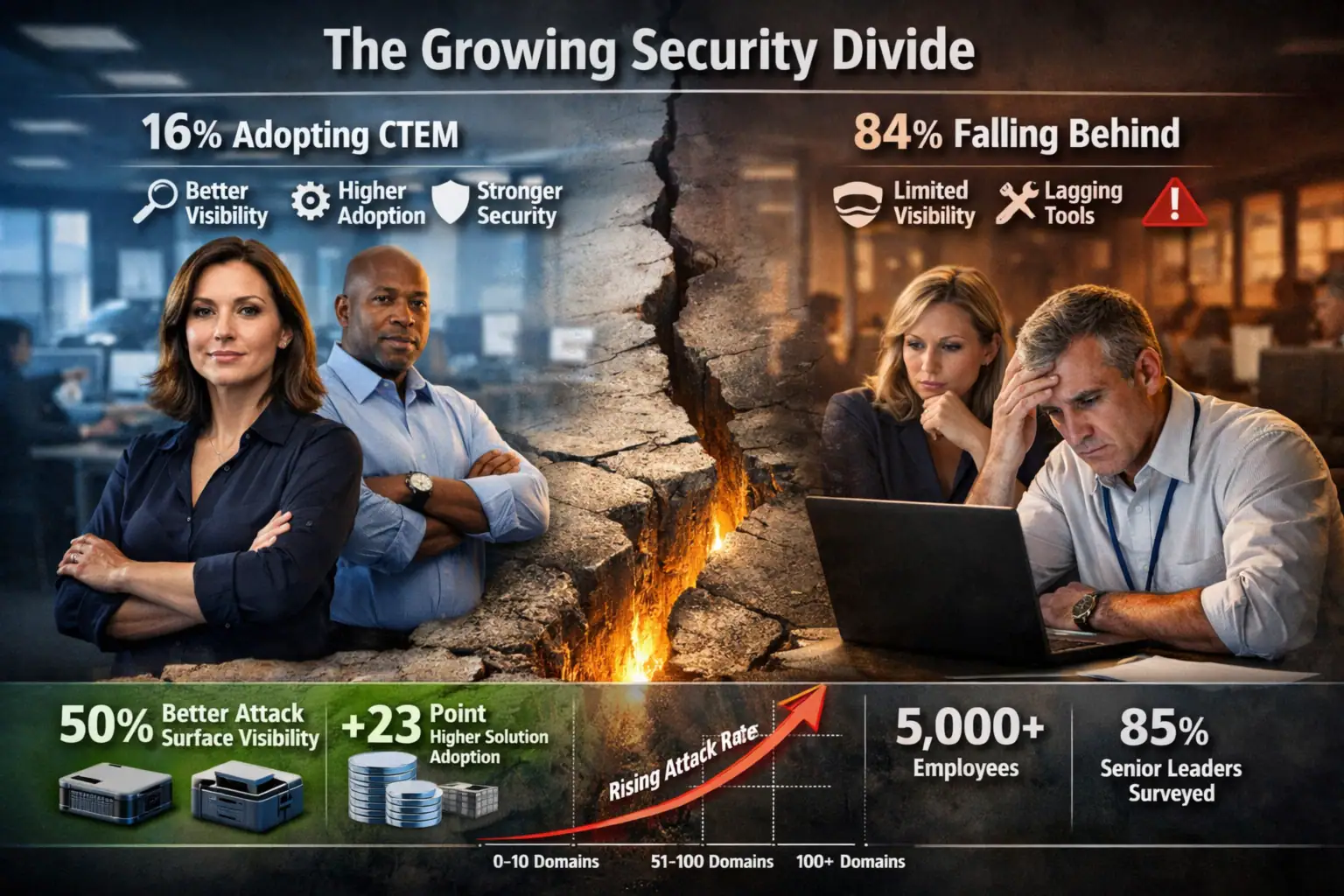
Continuous Threat Exposure Management (CTEM): The New Divide in Enterprise Cybersecurity
A recent 2026 market study of 128 senior security decision‑makers reveals a clear split between enterprises that have adopted Continuous ...

AI-Generated Passwords Are Not Secure: New Research Exposes LLM Password Weaknesses
Large language models such as ChatGPT, Claude and Gemini are increasingly being used not only for text generation, but also ...

Google Chrome Zero-Day CVE-2026-2441: What You Need to Know About the Latest Critical Browser Vulnerability
Google has released an out-of-band Chrome security update to fix CVE-2026-2441, the first publicly known Chrome zero-day vulnerability of 2026. ...

Microsoft 365 Copilot Bug Bypasses DLP and Sensitivity Labels for Confidential Emails
A recently identified bug in the corporate version of Microsoft 365 Copilot allowed the AI assistant to read and summarize ...

Mamont Android Banking Trojan Uses Fake Telegram Accelerator to Target Users
A new malicious campaign involving the Mamont Android banking trojan is actively targeting users, exploiting fake “Telegram accelerator” apps to ...






